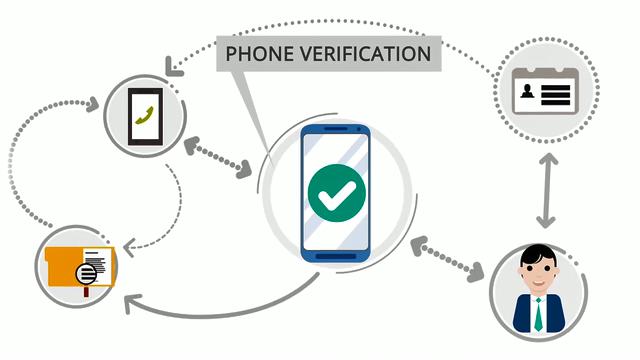
Mobile technology with fresh emerging concepts is becoming increasingly inexpensive and vital in society. The security violations of spammers and scammers are increasing for companies. The phone violation can lead to a bad customer experience or, worse, they can have detrimental effects on the brand, resulting in legal and financial impacts. A fantastic approach is to regularly use telephone checks at each stage of the customer’s life to check phone numbers to reduce the risk for compromised safety.
In the case of identification verification, active phone numbers might be quite useful. It is difficult to validate phone numbers because telecommunications authorities have been too creative in using the limited number range available and because telephone numbers differ in other nations. The mobile number is the last means to verify their identification with trillions of mobile telephone numbers registered worldwide. Some good approaches for user management enhance safety and client acquisition and retainment using mobile phone verification:
Registration authentication –
Phone verification may help validate identification, if a new user registers for their application, to ensure the new user claims to be. For example, if a new user downloads and records an app to the new account, a PIN is provided to a user registration user using a message service that may be input in the application on their device.
Authorize upgrades –
Many apps have a Freemium model so that the basic software is free to use, but they may access a premium version with a paid upgrade. Providing a PIN for checking and updating by mobile users can assist decrease erroneous downloads and curb fraudulent downloads.
Reset password –
When an applicator logs in from an unknown or alternative device and asks for a password reset, it can help to reduce fraud and identity robbery by delivering user identification verification codes. For example, when a login attempt originates from an unknown device Gmail uses this procedure to validate the identification using its cell phone name.
User Reactivation –
When an application or website user tries to sign in after a long period. A mobile phone check technique can again confirm that their use is true, not a hacker or spammer.
Refresh user details –
User profile information changes should always be confirmed with a simple notification connected to a mobile device. Ensuring that the owner of the account has made modifications is not only necessary for security purposes but also to provide users with accurate information. For example, an airline can only send vital customer flight details if they have current contact information.
Authenticate transaction –
Confirming real-time transactions substantially minimizes costly fraud resolution. Authentication of users via mobile phone checks at this key period is so powerful to reduce suspicious activities that there are numerous options for payment.
While something like phone validation may not appear to be particularly important at first. Once individuals begin to use it, they discover how much of an impact it can have on their business on a variety of levels.